Option 1: Reset DSRM Password with Ntdsutil
The Administrator password that you use when you start Recovery Console or when you press F8 to start Directory Service Restore Mode is stored in the registry-based Security Accounts Manager (SAM) on the local computer. The SAM is located in the %SystemRoot%\System32\Config folder. The SAM-based account and password are computer specific and they are not replicated to other domain controllers in the domain.
For ease of administration of domain controllers or for additional security measures, you can change the Administrator password for the local SAM. To change the local Administrator password that you use when you start Recovery Console or when you start Directory Service Restore Mode, use one of the following methods.
For additional information about how to secure the local SAM, click the article number below to view the article in the Microsoft Knowledge Base:
- On your machine, select Run from the Start menu, type ntdsutil and click OK.
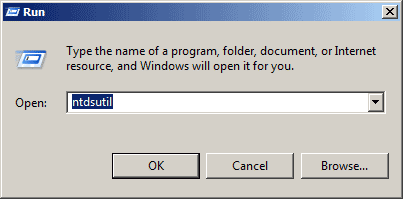
- At the Ntdsutil command prompt, type set dsrm password.
- At the DSRM command prompt, run the Reset Password command, passing the name of the server on which to change the password, or use the null argument to specify the local machine. For example, to reset the password on server thanos, enter the following command:
reset password on server thanos
To reset the password on the local machine, specify null as the server name:reset password on server null
- You'll be prompted twice to enter the new password.
- Type q to exit the DSRM command prompt.
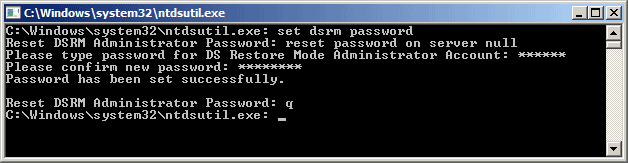
- At the Ntdsutil command prompt, type q to exit.
You can now use the local administrator account to log on to the recovery console or Directory Services Restore Mode using the new password. However, you can only use the Ntdsutil utility to reset DSRM password while logging into domain controller. If you also forgot domain administrator password, then you need to use the method below to change your forgotten DSRM password.
Option 2: Reset DSRM Password with PCUnlocker Utility
Option 2: Reset DSRM Password with PCUnlocker Utility
- You need an alternative computer with internet access to download the PCUnlocker utility.
- Unzip the download file, you'll get the pcunlocker.iso file.
- Burn the ISO image file to a CD or USB thumb drive using the ISO2Disc tool.
- Insert your newly burned CD/USB drive into the domain controller and power it up. Set the computer to boot from CD/USB by going into BIOS.
- Once you've gotten it to boot from the CD/USB, the computer will load the system inside the CD/USB drive and launch the PCUnlocker utility.
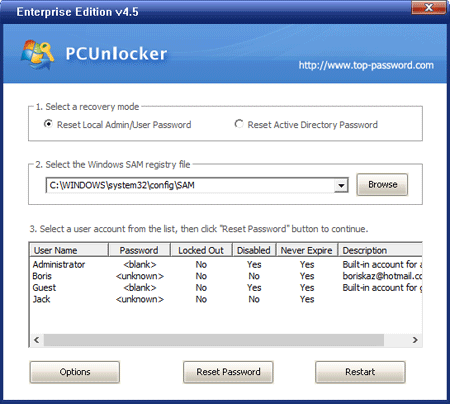
- Click on the Reset Local Admin/User Password option, you'll see the Windows SAM database and local user accounts.
- Choose the local administrator account and click on the Reset Password button.
- It will remove your forgotten DSRM password immediately.
Additionally, you can also use PCUnlocker utility to reset forgotten domain administrator password for Windows 2000 / 2003 / 2008 / 2012 Active Directory domain controllers.
The Administrator password that you use when you start Recovery Console or when you press F8 to start Directory Service Restore Mode is stored in the registry-based Security Accounts Manager (SAM) on the local computer. The SAM is located in the %SystemRoot%\System32\Config folder. The SAM-based account and password are computer specific and they are not replicated to other domain controllers in the domain.
For ease of administration of domain controllers or for additional security measures, you can change the Administrator password for the local SAM. To change the local Administrator password that you use when you start Recovery Console or when you start Directory Service Restore Mode, use one of the following methods.
Method 1
If Windows 2000 Service Pack 2 or later is installed on your computer, you can use the Setpwd.exe utility to change the SAM-based Administrator password. To do this:- Log on to the computer as the administrator or a user who is a member of the Administrators group.
- At a command prompt, change to the %SystemRoot%\System32 folder.
- To change the local SAM-based Administrator password, type setpwd, and then press ENTER.
To change the SAM-based Administrator password on a remote domain controller, type the following command at a command prompt, and then press ENTERsetpwd /s:servernamewhere servername is the name of the remote domain controller. - When you are prompted to type the password for the Directory Service Restore Mode Administrator account, type the new password that you want to use.
NOTE: If you make a mistake, repeat these steps to run setpwd again.
271641 The Configure Your Server Wizard Sets Blank Recovery Password
Method 2
- Log on to the computer as the administrator or a user who is a member of the Administrators group.
- Shut down the domain controller on which you want to change the password.
- Restart the computer. When the selection menu screen is displayed during restar, press F8 to view advanced startup options.
- Click the Directory Service Restore Mode option.
- After you log on, use one of the following methods to change the local Administrator password:
- At a command prompt, type the following command:net user administrator *
- Use the Local User and Groups snap-in (Lusrmgr.msc) to change the Administrator password.
- At a command prompt, type the following command:
- Shut down and restart the computer.
For additional information about how to secure the local SAM, click the article number below to view the article in the Microsoft Knowledge Base:
223301 Protection of the Administrator Account in the Offline SAM
NTDSUTIL Password Pull
Beginning with hotfix KB961320 on Windows Server 2008, you now have the option to synchronize the DSRM password on a DC with a specific domain account. You must do every time the password is changed; it does not create an automatic sync partnership.
1. Create a standard domain user account and set it with a complex password. It does not need to be a member of any special groups or the Domain Admins group.2. Install the hotfix on your DC and restart.3. Logon to the DC normally.4. In an elevated CMD prompt where you have logged on as a Domain Admin, run:NTDSUTIL SET DSRM PASSWORD SYNC FROM DOMAIN ACCOUNTQ Q
So for example (using NTDSUTIL’s ability to pass in all parameters on a single command-line):
Note how there is no need to provide the actual password being used, or provide the old password. This feature will also be included in Service Pack 2 for Win2008.
Group Policy Preference Automation of NTDSUTIL
So what if we want to automate this NTDSUTIL command so that is run via a scheduled task? This is easily done using Group Policy Preferences.
Note: Before you get too excited that I’ve missed something – no, GPP Local User password does not work with the DSRM passwords on domain controllers. You cannot use it to push a new password to the local administrator on DC’s; it only works only on member computers. Trust me, I’ve tried.
The beauty of this solution is that there is no password stored anywhere except in Active Directory itself and the system effectively self maintains – the only administrator intervention needed is to periodically change the special user’s password, and to make sure the scheduled task is working on the DC’s. The same way you should be checking to make sure those backups will actually function for a restore if you ever need to use this password.
So let’s set this up:
1. Start GPMC on a Windows Server 2008 or Windows Vista computer running RSAT.2. Create and link a new policy on the Domain Controllers OU (you are doing all this in a test domain first, right?).
3. Create the GPP Scheduled task settings.Note here that I have set:
A) Action of ‘Update’ (this will create the task if it does not exist).B) Run command of the built-in GPP variable for %SystemDir% to specify the System32 directory, along with the ntdsutil.exe to be called.C) The command line exactly as it would be done by hand with ntdsutil, including the quotation marks:“SET DSRM PASSWORD” “SYNC FROM DOMAIN ACCOUNT DsrmUser” Q QD) The task is Enabled with a checkbox so that it will run, not just be created.
E) Then I have set this to run as a daily task at 9AM (it’s fairly likely that the DC will be running at that point). I could also run this hourly, weekly, etc – whatever I want.
4. After having created the policy and letting it apply to DC’s, I now see it is working by examining the scheduled tasks on one of my domain controllers. There it is (as well as another one I added to run every night too – can’t be too careful):
5. Once the right time has come and gone, I boot a DC into DS Repair mode and check – sure enough, my new password has taken affect automagically.






No comments:
Post a Comment